
Securing Cloud Assets, Data & Edge Infrastructure
Cloud Native Full Stack Application and Infrastructure Security, Threat Intelligence, Vulnerability Management, Monitoring
REQUEST A QUOTE


Cloud Native Full Stack Application and Infrastructure Security, Threat Intelligence, Vulnerability Management, Monitoring
REQUEST A QUOTE

CyberEdge Continuous Monitoring Program provide controls inheritance for the auditing, risk assessment, incident response control requirements. We provide control documentations in your bespoke Cloud Security Plan (CSP).

Whether your framework is NIST 800.53, 171, 190 and CMMC L2-L5 we can design the guardrails, requirements in your Cloud Security Plan (CSP).
Our designs become functional frameworks that we translate into automated Threat Hunting and Advanced Log Management

Real-time Security Scanning, Monitoring, Vulnerability Management with 24/7 CSOC & IR services. We enable you to meet these requirements by providing best Secure Coding practices and Security Controls your team can inherit and document
CyberEdge

CyberE dge - Securing Data and Cloud Edge Services
Data Governance, Data Privacy, Data Tokenization, Data Assurance, Leveraging data intelligence to drive access parity
The security of your data in the cloud is crucial. We secure at scale in the cloud, Identity and Access Management, Encryption and Network Vulnerability & Pen Testing,


Monitor Cloud Identity, Virtual Machines, API Access and other vulnerabilities. Manage risk to authorized assets and services.
Threat Intel and Forensics
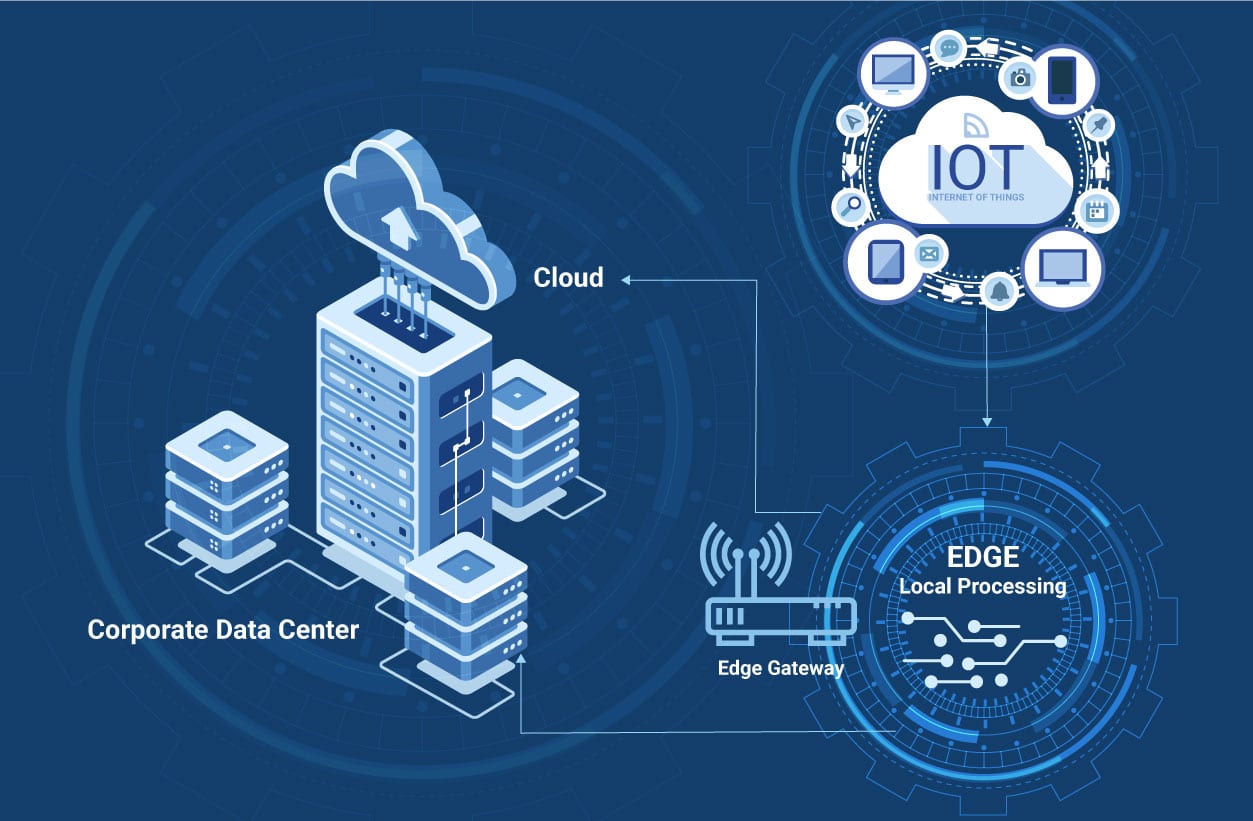

Blockchain technology can offer important cybersecurity benefits, such as reducing cyberattacks, and it has recently created a lot of hype as a panacea for all the current challenges related to information security.
Is your Cyber & IT Security Organization Ready?
cloud & cyber edge assessment2022 CyberEdge - Cyber Security Systems
Get industry relevant Ai, Cloud, Cyber, Data, DevOps, Infrastructure Security Certs
Earn industry relevant certs at your own pace
created with
Static Site Generator .